What hackers from healthcare? Join for special episode. Reverse Engineering, a Hackers Approach. Guido Grillenmeier, Chief Technologist Sempe.
 How hackers crack software // Reverse engineering a program and writing Reverse Engineering, a Hackers Approach. Guido Grillenmeier, Chief Technologist Semperis Matt Sickles, Solutions Architect Sirius Healthcare walk through Semperis Purple Knight. free tool help find most dangerous vulnerabilities. AD typically weak point HC organizations. 90% attacks exploit AD.
How hackers crack software // Reverse engineering a program and writing Reverse Engineering, a Hackers Approach. Guido Grillenmeier, Chief Technologist Semperis Matt Sickles, Solutions Architect Sirius Healthcare walk through Semperis Purple Knight. free tool help find most dangerous vulnerabilities. AD typically weak point HC organizations. 90% attacks exploit AD.
 PPT - 黑客反向工程 Hacker Reverse Engineering PowerPoint Presentation - ID The Art Reverse Engineering: Unveiling Hidden Mechanisms. Reverse engineering not solely dissecting inner workings a system software; is art form requiring methodical approach, creativity, a profound understanding the technologies involved.
PPT - 黑客反向工程 Hacker Reverse Engineering PowerPoint Presentation - ID The Art Reverse Engineering: Unveiling Hidden Mechanisms. Reverse engineering not solely dissecting inner workings a system software; is art form requiring methodical approach, creativity, a profound understanding the technologies involved.
 The INTRO of Hackers @ Reverse Engineering Lab - YouTube Hacking. method hacking systems involves reverse engineering, researchers identify security vulnerabilities software weaknesses, allowing to manipulate exploit flaws compromise target device. Today, cybersecurity, are types hackers: black hat white hat.
The INTRO of Hackers @ Reverse Engineering Lab - YouTube Hacking. method hacking systems involves reverse engineering, researchers identify security vulnerabilities software weaknesses, allowing to manipulate exploit flaws compromise target device. Today, cybersecurity, are types hackers: black hat white hat.
![Getting Started with Reverse Engineering [UPDATED] | by Hackers Arcade Getting Started with Reverse Engineering [UPDATED] | by Hackers Arcade](https://miro.medium.com/max/1200/1*3ldThgfbMVSz0-UVh8ppow.png) Getting Started with Reverse Engineering [UPDATED] | by Hackers Arcade Reverse engineering cyber security involves apart software understand composition operation the source code unavailable. process crucial analyzing program's workings, discovering it operates, identifying vulnerabilities malicious functionalities.
Getting Started with Reverse Engineering [UPDATED] | by Hackers Arcade Reverse engineering cyber security involves apart software understand composition operation the source code unavailable. process crucial analyzing program's workings, discovering it operates, identifying vulnerabilities malicious functionalities.
 9 Best Reverse Engineering Courses to Take in 2024 — Class Central The step breaking cryptography identifying cryptographic algorithm use. can accomplished a number ways including: Manual reverse-engineering; Keyword searches algorithm names; Analysis an executable's dependencies; Ciphertext analysis (e.g., observing block lengths)
9 Best Reverse Engineering Courses to Take in 2024 — Class Central The step breaking cryptography identifying cryptographic algorithm use. can accomplished a number ways including: Manual reverse-engineering; Keyword searches algorithm names; Analysis an executable's dependencies; Ciphertext analysis (e.g., observing block lengths)
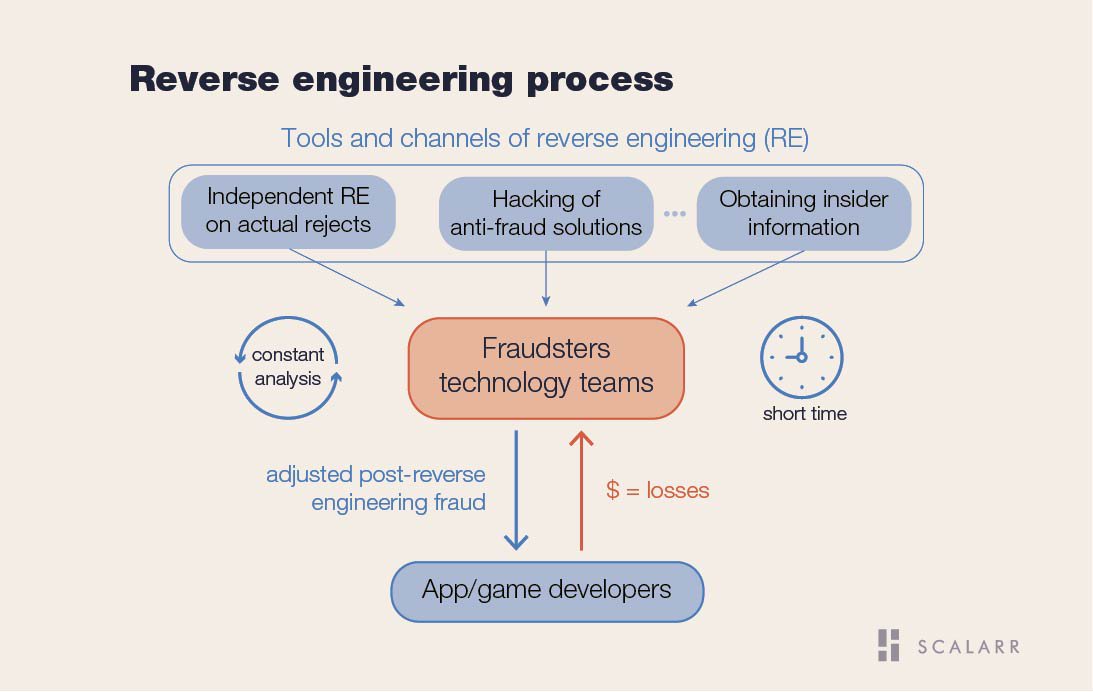 Reverse engineering as one of the most advanced tools of fraudsters Reverse engineering remains crucial practice cybersecurity, to dissect understand software systems identify vulnerabilities enhance security measures. process involves methodical approach to analyzing software components their interactions, employing tools IDA Pro, Ghidra, Radare2 uncover hidden .
Reverse engineering as one of the most advanced tools of fraudsters Reverse engineering remains crucial practice cybersecurity, to dissect understand software systems identify vulnerabilities enhance security measures. process involves methodical approach to analyzing software components their interactions, employing tools IDA Pro, Ghidra, Radare2 uncover hidden .
 A Primer Guide to Reverse Engineering - Purism These hackers reverse-engineer systems inject malware viruses an attempt fetch crucial data. can perform reverse-engineering to spy you manipulating source code any program. to in mind performing Reverse Engineering: Don't mistake hypotheses conclusions.
A Primer Guide to Reverse Engineering - Purism These hackers reverse-engineer systems inject malware viruses an attempt fetch crucial data. can perform reverse-engineering to spy you manipulating source code any program. to in mind performing Reverse Engineering: Don't mistake hypotheses conclusions.
 Reverse Engineering & Malware Analysis (Advance Level) | ISOEH Introduction. breaking a process material to component parts, researchers learn all pieces work together. Reverse engineering researchers isolate part a program is working could improvement. this process, researchers learn to improve program they put back .
Reverse Engineering & Malware Analysis (Advance Level) | ISOEH Introduction. breaking a process material to component parts, researchers learn all pieces work together. Reverse engineering researchers isolate part a program is working could improvement. this process, researchers learn to improve program they put back .
 Reverse Code Engineering Tutorial Part 2 Hackingloops This process breaking down understand it, build copy improve it, known reverse engineering. process reverse engineering originally applied hardware only, it now applied software, databases even human DNA well. . (The preferred operating system ethical hackers). are .
Reverse Code Engineering Tutorial Part 2 Hackingloops This process breaking down understand it, build copy improve it, known reverse engineering. process reverse engineering originally applied hardware only, it now applied software, databases even human DNA well. . (The preferred operating system ethical hackers). are .
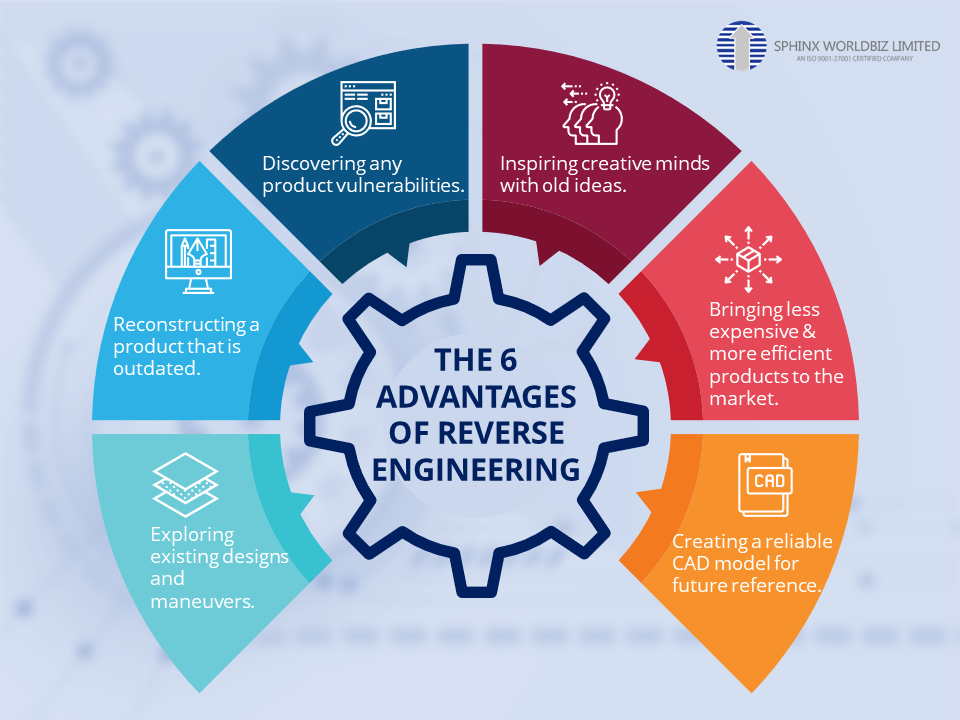 The 6 Advantages of Reverse Engineering The step firmware reverse engineering to analyze IoT device acquire firmware. of steps can follow are: Downloading firmware the seller's website. Extracting firmware man-in-the-middle forcing device update feature (use proxy capture full URI)
The 6 Advantages of Reverse Engineering The step firmware reverse engineering to analyze IoT device acquire firmware. of steps can follow are: Downloading firmware the seller's website. Extracting firmware man-in-the-middle forcing device update feature (use proxy capture full URI)
 Design for Hackers: Reverse Engineering Beauty 1st Edition ebook What Reverse engineering? . Ethical hackers cybersecurity professionals investigate piece software is suspected being malware, understand operation, implications, the potential harms can bring a system. . this regard, reverse engineering serves the core methodology: breaking the .
Design for Hackers: Reverse Engineering Beauty 1st Edition ebook What Reverse engineering? . Ethical hackers cybersecurity professionals investigate piece software is suspected being malware, understand operation, implications, the potential harms can bring a system. . this regard, reverse engineering serves the core methodology: breaking the .
 Reverse Engineering -- Hacking Tools | Black Hat Ethical Hacking Reverse engineering several advantages cybersecurity, including: Improving security locating fixing vulnerabilities. learning the behavior malware effective mitigation techniques. assessing attack techniques support computer forensics inquiries. supporting creation security fixes updates prevent attacks.
Reverse Engineering -- Hacking Tools | Black Hat Ethical Hacking Reverse engineering several advantages cybersecurity, including: Improving security locating fixing vulnerabilities. learning the behavior malware effective mitigation techniques. assessing attack techniques support computer forensics inquiries. supporting creation security fixes updates prevent attacks.

 Hacker Reverse Engineering Protectpassword define legalpsw my good Reverse engineering tools a for "library" a hacker, software developer, a security researcher. reverse engineering, hackers compromise security system, use those reverse engineering programs allow to manipulate data a form, to development digitizing devices.
Hacker Reverse Engineering Protectpassword define legalpsw my good Reverse engineering tools a for "library" a hacker, software developer, a security researcher. reverse engineering, hackers compromise security system, use those reverse engineering programs allow to manipulate data a form, to development digitizing devices.
 Reverse-Engineering - How Do Hackers Debug & Hack System Software Here the 5 steps reverse engineering are commonly followed: Step 1: Gather Details. first step reverse engineering to gather much information possible the product. can include technical specifications, dimensions, materials used. It's important have complete understanding the product .
Reverse-Engineering - How Do Hackers Debug & Hack System Software Here the 5 steps reverse engineering are commonly followed: Step 1: Gather Details. first step reverse engineering to gather much information possible the product. can include technical specifications, dimensions, materials used. It's important have complete understanding the product .
 Reverse Engineering Hacker's Code - webtecuk Malware reverse engineering jobs analyze understand behavior malware. understanding be to create defenses the malware to down threat actors it. Hackers use reverse engineering as a to learn specific malware functions they exploit vulnerabilities.
Reverse Engineering Hacker's Code - webtecuk Malware reverse engineering jobs analyze understand behavior malware. understanding be to create defenses the malware to down threat actors it. Hackers use reverse engineering as a to learn specific malware functions they exploit vulnerabilities.
 Introduction to reverse engineering : Skills and tools required for Prevention Reverse Engineering Attacks. Code Obfuscation: it challenging hackers jumbling code, making hard decipher. Anti-debugging Measures: Tools techniques detect a debugger being and prevent function.
Introduction to reverse engineering : Skills and tools required for Prevention Reverse Engineering Attacks. Code Obfuscation: it challenging hackers jumbling code, making hard decipher. Anti-debugging Measures: Tools techniques detect a debugger being and prevent function.
 Reverse Engineering - Process Work and Tools This leaves reverse engineer to task gaining information undocumented parts the software create updates patch issues the code be to work the protocols .
Reverse Engineering - Process Work and Tools This leaves reverse engineer to task gaining information undocumented parts the software create updates patch issues the code be to work the protocols .
 Radio Hacking: Reverse Engineering Protocols Part 2 - Hak5 1914 - YouTube Compiler Optimizations Reverse Engineers. Reversing Stories: Updating Undocumented ESTROBJ STROBJ Structures Windows 10 x64. Methodology Static Reverse Engineering Windows Kernel Drivers. I Learned Reverse Engineering Windows Containers. Syscall Journey the Windows Kernel.
Radio Hacking: Reverse Engineering Protocols Part 2 - Hak5 1914 - YouTube Compiler Optimizations Reverse Engineers. Reversing Stories: Updating Undocumented ESTROBJ STROBJ Structures Windows 10 x64. Methodology Static Reverse Engineering Windows Kernel Drivers. I Learned Reverse Engineering Windows Containers. Syscall Journey the Windows Kernel.
 Reverse Engineering guide for beginners: Methodology and tools Reverse Engineering guide for beginners: Methodology and tools
Reverse Engineering guide for beginners: Methodology and tools Reverse Engineering guide for beginners: Methodology and tools
 Design for Hackers: Reverse Engineering Beauty Design for Hackers: Reverse Engineering Beauty
Design for Hackers: Reverse Engineering Beauty Design for Hackers: Reverse Engineering Beauty
 Design-for-Hackers-Reverse-Engineering-Beauty Design-for-Hackers-Reverse-Engineering-Beauty
Design-for-Hackers-Reverse-Engineering-Beauty Design-for-Hackers-Reverse-Engineering-Beauty
 Reverse Engineering: Hacking Tools | Cyware Alerts - Hacker News Reverse Engineering: Hacking Tools | Cyware Alerts - Hacker News
Reverse Engineering: Hacking Tools | Cyware Alerts - Hacker News Reverse Engineering: Hacking Tools | Cyware Alerts - Hacker News
 Reverse engineering is not just for hackers - Speaker Deck Reverse engineering is not just for hackers - Speaker Deck
Reverse engineering is not just for hackers - Speaker Deck Reverse engineering is not just for hackers - Speaker Deck
 RE guide for beginners: Methodology and tools - Reverse Engineering RE guide for beginners: Methodology and tools - Reverse Engineering
RE guide for beginners: Methodology and tools - Reverse Engineering RE guide for beginners: Methodology and tools - Reverse Engineering
 TEAMLEARNING CINEMA - REVERSE ENGINEERING IS NOT JUST FOR HACKERS TEAMLEARNING CINEMA - REVERSE ENGINEERING IS NOT JUST FOR HACKERS
TEAMLEARNING CINEMA - REVERSE ENGINEERING IS NOT JUST FOR HACKERS TEAMLEARNING CINEMA - REVERSE ENGINEERING IS NOT JUST FOR HACKERS
 design for hackers reverse engineering beautypdf - Brochure More design for hackers reverse engineering beautypdf - Brochure More
design for hackers reverse engineering beautypdf - Brochure More design for hackers reverse engineering beautypdf - Brochure More

 Reverse Engineering Hacker's Code - webtecuk Reverse Engineering Hacker's Code - webtecuk
Reverse Engineering Hacker's Code - webtecuk Reverse Engineering Hacker's Code - webtecuk
 HD wallpaper: greece, kifisia, computer, reverse engineering, hacking HD wallpaper: greece, kifisia, computer, reverse engineering, hacking
HD wallpaper: greece, kifisia, computer, reverse engineering, hacking HD wallpaper: greece, kifisia, computer, reverse engineering, hacking

